Power generation, storage, transmission, and distribution service providers are legally bound to meet NERC CIP standards. This post explores strategies to achieve compliance with respect to operational data systems.
Unlock the full potential of big data with dataPARC’s tools and features.
Standards for Critical Infrastructure Protection (CIP) have been developed by the North American Electric Reliability Corporation (NERC) to minimize the risk of electric service interruptions in the North American continent’s bulk energy system. Although initially voluntary, utility companies are now legally bound to meet these standards, including those related to operational data security and availability.
Robust, available operational data systems are pivotal to the efficiency, reliability, and profitability of electrical infrastructure assets. Continuous system monitoring, abnormal condition alerts, long-term performance reporting and downtime root-cause analysis are just a few essential functions that rely on powerful data visualization and analysis tools connected to a solid data historian foundation.
Unfortunately, these data systems can also pose risks if not implemented carefully. NERC CIP standards serve as a framework for designing secure operational data systems with low risk of adverse incident impacts. Ensuring software compliance with these and other critical infrastructure regulations is a key consideration when evaluating and deploying industrial data solutions.
NERC CIP Standards
Although aspects of many NERC CIP standards may apply to operational data systems, we will focus on a short list that are likely to require the most attention:
Personnel and Training (CIP-004):
This standard requires that only properly trained personnel are allowed access to critical data systems, and that only the minimum access required per job function is provided. An operational data system should require secure login and role-based access management with sufficient granularity so that employees only interact with data needed to accomplish their work tasks.
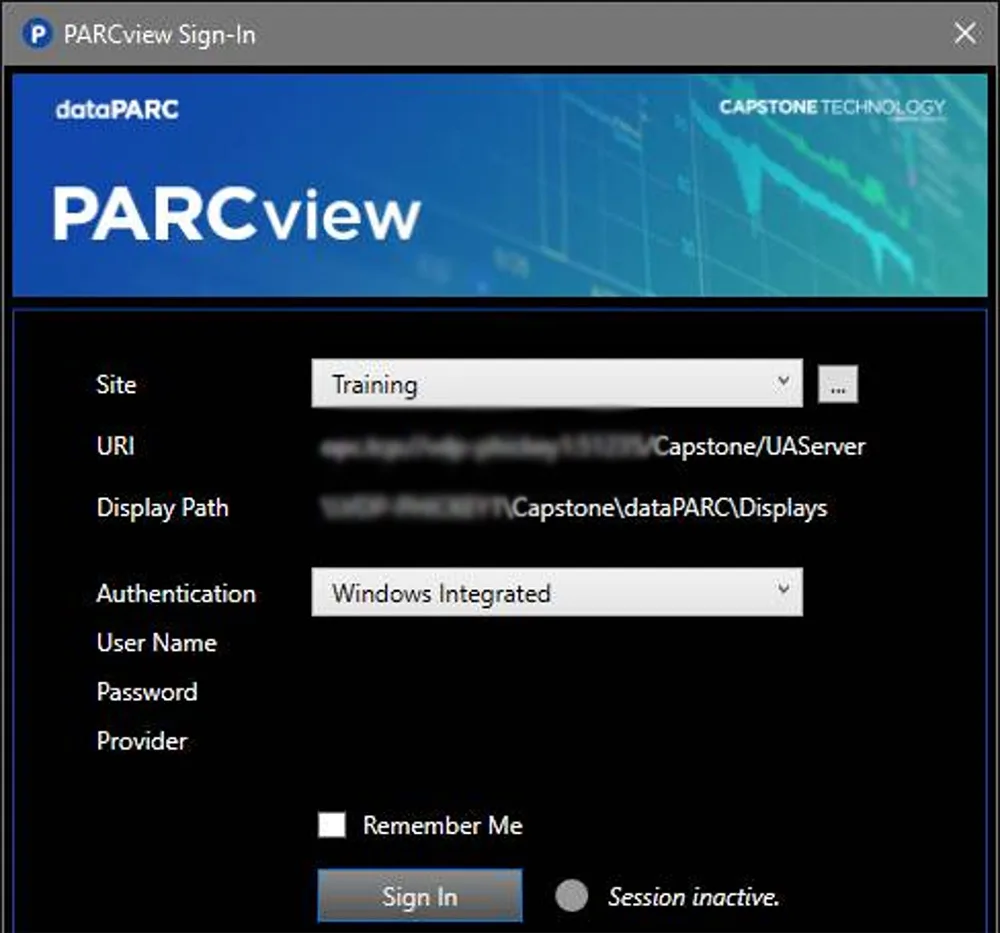
Often limiting personal to operational systems includes the utilization of logins and authentication types such as windows integrated authentication.
Electronic Security Perimeters (CIP-005):
System architecture must be designed so that operational data is contained within a secure perimeter. In some cases, this can mean an “air-gapped” operational technology (OT) network with no connection to the internet or any other outside network. Even if air-gapping is not required, a carefully managed firewall should be employed to separate the OT network from external systems. Operational data systems must be capable of functioning independently within the electronic security perimeter.
Physical Security (CIP-006):
Operational data system hardware and access points must be physically secured against intentional or accidental damage. This includes data centers, virtual servers, user workstations, etc. This standard has implications when deciding whether to host operational data on-premises local to the asset, at a central corporate server, or in the cloud. Physical security is most easily achieved and monitored on company premises; cloud hosted systems may introduce difficulty ensuring physical security.
Recovery Plans (CIP-009):
NERC’s system recovery standard may require more than a basic data backup strategy. Data collection redundancy, high-availability historians with automatic failover, and RAID storage configurations may be necessary to facilitate swift and complete recovery of operational data following an adverse event.
Information Protection (CIP-011):
Within an operational data system, the data itself must be protected from both unauthorized access and manipulation. Although the access management and physical security measures covered by other standards may mitigate these risks, data encryption may be required, both at-rest and in-transit. Modern, standard, supported protocols should be used for data communication both between the assets and the historian, as well as between the historian and the visualization/analysis software tools.
Supply Chain Risk Management (CIP-013):
The operational data system vendor plays an important role in meeting the NERC CIP standards. Vendors should demonstrate clear commitment to cyber security, including continued development of and support for the operational data software. Security patches should be promptly and readily available. Consideration should also be given to the level of continuous remote system access required by the vendor. Can the operational data software be licensed and run without any connection to the vendor?
Check out dataPARC’s real-time process data analytics tools & see how better data access can help your business.
dataPARC in a NERC-Regulated Environment:
dataPARC’s operational data historian and visualization/analysis tools offer a host of features that make NERC CIP standard compliance easy.
dataPARC Security:
dataPARC’s role-based access management tool, the dataPARC Security Console, provides a flexible framework for controlling access to data, features, and system configuration. Access is fully granular with respect to each display type and individual data tag. dataPARC Security can be integrated with Microsoft Active Directory for single sign-on, or it can act as its own identity provider. User groups and role-based access can be configured across the system.
On-Premises Architecture:
dataPARC is typically hosted on-premises and offers flexible hardware options including “bare metal” servers or virtual machines. Data collection, historical archives, and data processing applications are all installed and stored on customer-owned infrastructure, requiring no connection to external systems for operation or licensing. dataPARC often runs on “air-gapped” or firewalled networks.
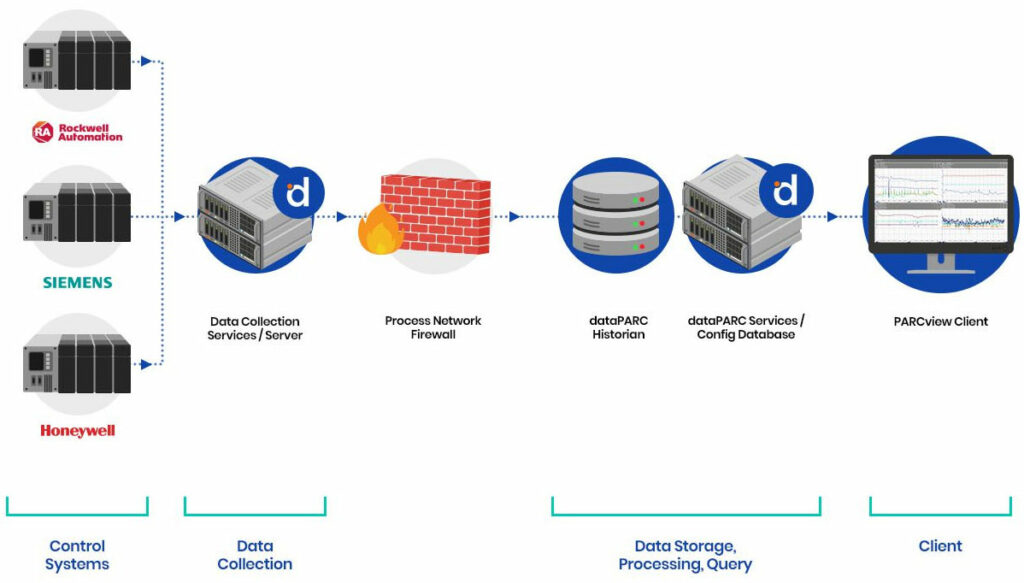
This is an example of a standard implementation of the dataPARC Historian and visualization tools.
OT/IT Network Separation:
dataPARC only requires two open ports in the firewall between the data collector on the OT network and the dataPARC Historian, which may reside in a network “DMZ” or on the business (IT) network. Use of a “data diode” is also supported between the OT devices and the data collector node when absolute assurance of one-way data traffic is required.
Data/System Redundancy:
Redundant data collection from OT devices can be configured for automatic fail-over, reducing the risk of missing historical data in the event of OT device or network failure. dataPARC also offers a High-Availability historian option, providing full data storage and access redundancy. Lastly, the dataPARC application server can be installed using various RAID hard drive configurations or even a fully mirrored secondary server.
Data Encryption:
From the OT data source to the end-user display, dataPARC provides modern data encryption both in-transit and at-rest. OPC UA and gRPC protocols are utilized for data transit, both offering industry-standard encryption methods. Data are also encrypted within the dataPARC Historian’s long-term archive files. The diagram below provides an example of data transfer protocols and encryption stages.
Final Thoughts: Building Secure, Compliant Operational Data Systems
Meeting NERC CIP standards isn’t a checkbox exercise, it’s a foundational part of building resilient, secure, and future-proof operational data infrastructure in the power industry. As cyber threats grow and compliance requirements evolve, utilities must ensure their systems are not only functional and reliable, but also aligned with software compliance best practices for critical infrastructure.
With the right tools and architecture in place, utility providers can confidently navigate NERC CIP requirements while gaining meaningful visibility and control over their operations. Solutions like dataPARC demonstrate how compliance and performance can go hand in hand.

Learn more about dataPARC and Request a Demo Today!